Juniper Crack Password
Dec 21, 2015 How to log into any backdoored Juniper firewall – hard-coded password published Did the NSA knacker ScreenOS? Probably not. By Iain Thomson in San Francisco 21 Dec 2015 at 20:29. ACX Series,M Series,MX Series,T Series,PTX Series,EX Series,SRX Series. Recovering the Root Password on Routers, Recovering the Root Password on Junos OS with Upgraded FreeBSD, Recovering the Root Password for Junos OS Evolved, Recovering the Root Password on Switches.
Juniper Password Decryptor is a software application that provides users with a simple means of recovering their lost passkeys from Juniper routers.
The installation process does not last long, yet it is important to note that it offer to download some third-party products. After completing it, you come face to face with a straightforward GUI, which is only comprised of a few buttons and some boxes which display various information.
Download Juniper Password Decryptor Crack & Serial
In addition to that, extensive Help contents are provided online, thus ensuring that all types of users can find their way around it without encountering any issues.
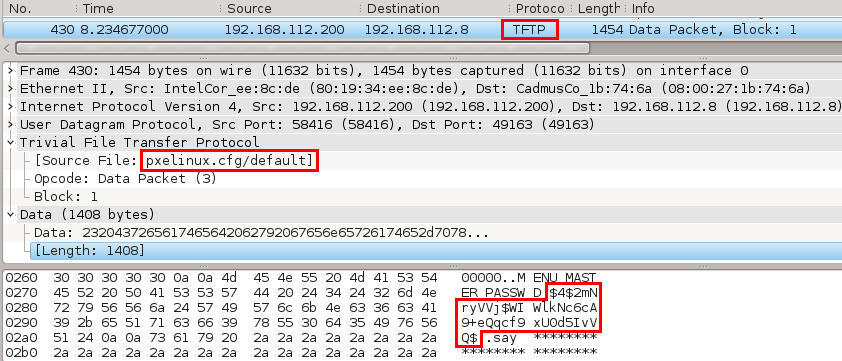
This utility enables you to decrypt Juniper $9$ passwords using two methods. To be more accurate, you can easily paste the password in the main window and click the “Decrypt Password” button, while it is also possible to upload the configuration file from the hard drive.
The result can be copied to the Clipboard with just a click of the button, so that you can store it in a document or another program for safekeeping. No other notable options are incorporated.
CPU and memory usage is low at all times and therefore the computer’s performance is not going to be burdened in any way and you can run it alongside other apps with great ease. The interface is suitable to all types of users, including beginners, tasks are completed in a timely manner and our tests did not reveal any errors, crashes or bugs.
Taking all of this into consideration, we can safely say Juniper Password Decryptor Crack is a pretty efficient piece of software. If you are interested in skipping the installation process, you should know a portable edition is also available, called Portable Juniper Password Decryptor Crack.
Juniper Password Decryptor related software
| Rating | 3.0 |
| Downloads | 6735 |
| Package size | 308 KB |
| Supported systems | Windows XP, Windows Vista, Windows 7, Windows 7 64 bit, Windows 8, Windows 8 64 bit |
| Company |
Comments for Juniper Password Decryptor crack
Diana, 25 July 2018謝謝Juniper Password Decryptor破解
Tommaso, 19 February 2018спасибо за кряк для Juniper Password Decryptor
Donald, 12 October 2017Thanks a lot for sharing Juniper Password Decryptor!
lucrezia, 11 May 2017Yippee! thanks for the keygen
Last month, it was revealed that Juniper Networks' routers/firewalls. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. Government agencies and officials could have been compromised over the last three years.Although Juniper says that they discovered the 'backdoor' through routine auditing, evidence would seem to be contrary to that claim. In addition, Juniper reported that the attacker could wipe the security logs (this means the backdoor had root or sysadmin privileges) so that there is no sign of the breach. Juniper and others have speculated this attack was promulgated by a foreign government, maybe Russia or China.
Image by Ken Wolter/Juniper Networks is a very large (nearly $5 billion in annual revenue) Silicon Valley-based networking gear manufacturer. Not as big as Cisco, the global leader, but large enough to have their equipment used around the world (37% of the global market). They manufacture routers, switches, and network security equipment.Some consider Juniper a leader in secure communication technology.
Their products are widely used in the U.S. And Europe, but more importantly, they are widely deployed in Pakistan, Yemen.
And China, countries of particular interest to U.S. Espionage agencies. VPNWhat was exposed in this hack was the VPN service. This is the virtual private network that allows people outside the network to securely connect into the internal network by authentication and encryption. If the VPN is hacked, then the traffic from those using the VPN service would be exposed to sniffing and, of course, eavesdropping. Image via What REALLY HappenedHere's what I suspect really happened. The NSA has been asking companies for backdoors on their security protocols for years.
In some cases, they have insisted that they be provided backdoors. They can be very persuasive. Some companies have complied and some have resisted.Since the Paris attacks last month, national security officials have been insisting that they be granted backdoors on all encrypted communication. This issue even surfaced in the recent U.S. Presidential debates.(As a side note here, the encrypted email service, ProtonMail, was DoSed just before the Paris attacks. Were the Paris attackers using ProtonMail to communicate and the security services them to keep anyone from using it?)Some experts have resisted these calls for backdoors insisting that if the NSA were granted a backdoor to these communications, then these backdoors might be used by others, not just the NSA. A backdoor is a backdoor.
If the NSA can use it, hackers can as well. The practice of backdoors reduces everyone's security.
Snowden Documents Reveal NSA Had Compromised JuniperIn a document released by NSA whistleblower Edward Snowden, named 'Assessment of Intelligence Opportunity - Juniper' the NSA and GCHQ (Britain's equivalent of NSA) revealed that they had found ways to penetrate the Juniper Netscreen product (it's a combination IDS and VPN).I suspect that the NSA had asked or insisted that Juniper implant a backdoor for themselves to spy on everyone's encrypted communication. Juniper complied by embedding this backdoor in their operating system and giving the NSA the keys to the kingdom.So, why did Juniper report this as a hack? Some hacker, likely a national government, found this backdoor and began to use it just like NSA was. When they discovered that others had found the backdoor, they had to close it and announce it as a hack. What Does This Mean to Us?What does all this mean to us?
First, don't assume that a VPN is safe. Many of these VPNs use Juniper or other vulnerable equipment.Second, as the NSA is implanting these network devices with backdoors, hackers and national espionage organizations will be looking for them. It might take days, weeks, or months of recon, but when they do, they will have total access to all the traffic across that brand of router around the world.
Les sims 3 animaux et cie cracked. This makes all of us less safe.Third, if you need access to encrypted communications, start looking for these embedded backdoors on products manufactured by U.S. Companies compromised by the NSA. Juniper is not the only one.- Learn How To Code with Null Byte's Beginner's Python Course. Sorry Phoenix750 but i don't agree really, you are right by saying that you are anonymous by discarding all technology of any kind.
But this only leaves no digital footprint of yourself, things that YOU yourself would do online. This does not apply for other instances that save your personal information on their servers (like banks, phone company's, your government.) I think if the right person wants to find you, he will find you! Even if you don't have a computer or a telephone! Because you use electricity, water, gas.
And for these you have to pay bills so i think that this is not the right approach on staying truly anonymous. If you want to be anonymous you should go live in greenland or alaska or some remote place were you do everything yourself (and not call the filmcrew to make a show about it)Just to be clear i mean no offence to you Phoenix750What i like to do when i do some coding or other stuff i don't want out there (yet) is use a fully offline machine, no networking capabilities on it whatsoever. So its only put to the test when its fully finished Reply.